For the first time since fdesetup‘s initial release in OS X Mountain Lion 10.8.x, Apple has not added new features to fdesetup as part of a new OS release. Instead, fdesetup maintains the same set of features in OS X El Capitan 10.11.x as it had in OS X Yosemite 10.10.x.
This decision may mean that fdesetup, an essential command-line tool for enabling, administering and disabling Apple’s FileVault 2 encryption, is now considered by Apple to be a fully-developed toolset for managing FileVault 2.
fdesetup gives Mac administrators the following command-line abilities:
- Enable or disable FileVault 2 encryption on a particular Mac
- Use a personal recovery key, an institutional recovery key, or both kinds of recovery key.
- Enable one or multiple user accounts at the time of encryption
- Get a list of FileVault 2-enabled users on a particular machine
- Add additional users after FileVault has been enabled
- Remove users from the list of FileVault enabled accounts
- Add, change or remove individual and institutional recovery keys
- Report which recovery keys are in use
- Perform a one-time reboot that bypasses the FileVault pre-boot login
- Report on the status of FileVault 2 encryption or decryption
I’ll be taking you through all of the capabilities mentioned above, with a focus on showing exactly how they work. See below the jump for details.
Enabling Filevault 2 Encryption For One Or Multiple Users
fdesetup is amazingly flexible when it comes to enabling FileVault 2 encryption from the command-line. To start with the simplest method, run the following command with root privileges to enable FileVault 2 encryption:
fdesetup enable
You’ll be prompted for the username and password of the primary user, which is the account you will work with at the FileVault 2 pre-boot login screen once the encryption is turned on.
If everything’s working properly, you’ll next be given an alphanumeric personal recovery key and prompted to restart.
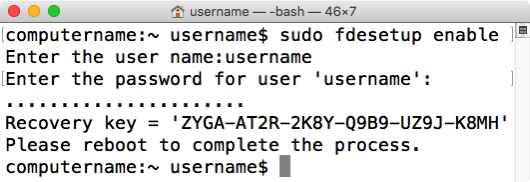
VERY IMPORTANT: The fdesetup-generated personal recovery key is not saved anywhere outside the machine. Make a record of it or you will not have a recovery key available to help unlock your Mac’s encryption in case of a problem.
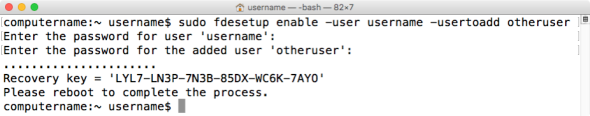
You can also enable additional user accounts at the time of encryption, as long as the accounts are either local or mobile accounts on the Mac being encrypted. Run the following command with root privileges to enable FileVault 2 and specify the accounts you want:
fdesetup enable -user username -usertoadd other_username -usertoadd yet_another_username
You’ll be prompted for the passwords of the accounts specified. After that, you’ll be given an alphanumeric personal recovery key and prompted to restart. All of the accounts specified should appear at the FileVault 2 pre-boot login screen.
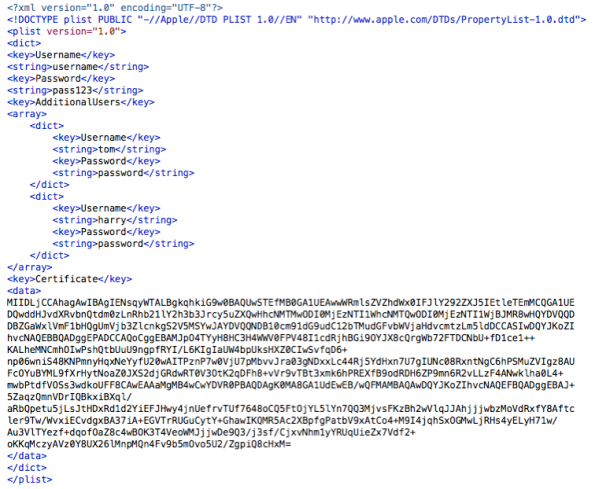
For those who want to automate the process, fdesetup also supports importing a properly formatted plist via a standard input stream (stdin). The plist needs to follow the format below:
Additional users can be included as needed by adding additional user information under the AdditionalUsers plist key.
Note: All account passwords need to be supplied in cleartext.
Once the plist has been set up and properly formatted, run the following command with root privileges to enable FileVault 2 encryption and reference the account information in the plist file:
fdesetup enable -inputplist < /path/to/filename.plist
Since the accounts and passwords are in the plist file, fdesetup does not need to prompt for passwords. Instead, the alphanumeric personal recovery key is displayed and the user is prompted to restart. All of the accounts specified in the plist file should appear at the FileVault 2 pre-boot login screen.
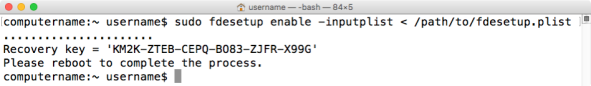
To avoid the need to enter a password, fdesetup also has a -defer flag in El Capitan that can be used with the “enable” command option to delay enabling FileVault 2 until after the current (or next) user logs out. With the -defer flag, the user will be prompted for their password at their next logout or restart. The recovery key information is not generated until the user password is obtained, so the -defer option requires a file location where this information will be written to as a plist file.
The property list file will be created as a root-only readable file and contain information similar to what’s show below.
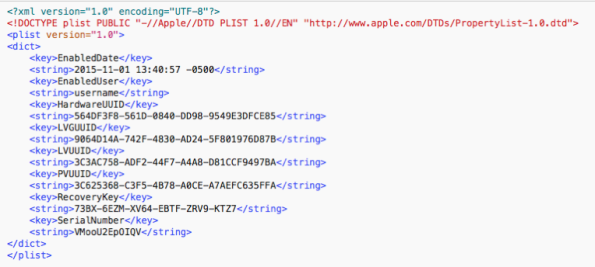
Note: For security reasons, the plist file with the recovery key information should not stay on the encrypted system. Please copy it to a safe location and then securely delete this plist file from the encrypted system.
Run the following command with root privileges to defer enabling FileVault 2 and specify the account you want:
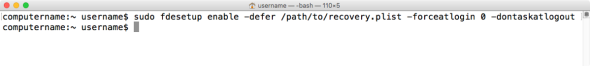
fdesetup enable -user username -defer /path/to/filename.plist
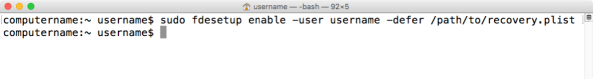
If there is no user account specified with the -user option, then the current logged-in user will be enabled for FileVault 2. If there is no user specified and no users are logged in when the command is run, then the next user that logs in will be chosen and enabled.
If you don’t want to specify the account, run the following command with root privileges:
fdesetup enable -defer /path/to/filename.plist
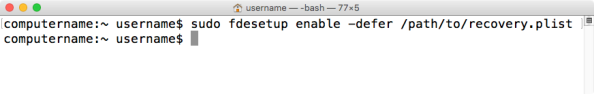
On logout, the user will be prompted to enter their account password.
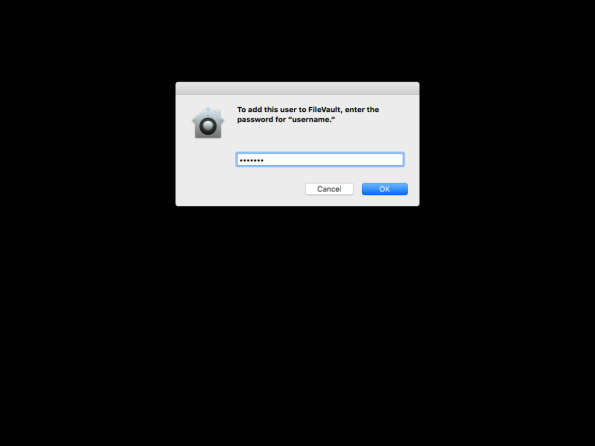
Once entered, FileVault 2 will be enabled and the recovery information plist file will be created. Once the enabling process is complete, the Mac will restart.
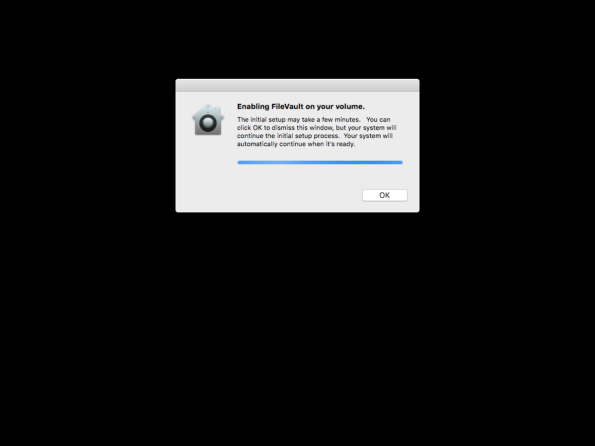
In addition to enabling FileVault 2 as part of the logout process, Apple added the ability to set a deferred enablement at login to OS X Yosemite. In OS X El Capitan, this means that Mac admins can set a deferred enablement with the following options:
- Enforce FileVault 2 enablement at logout
- Enforce FileVault 2 enablement at login
- Enforce FileVault 2 enablement at both login and logout
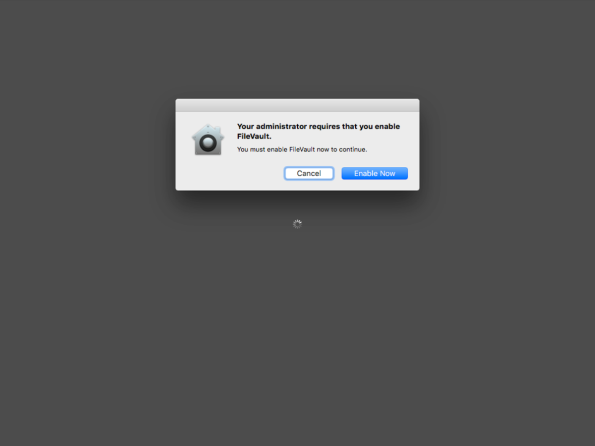
To set a deferred enablement at login, the following options may be added to fdesetup‘s -defer flag:
- -forceatlogin max_cancel_attempts
- -dontaskatlogout
These additional options allow a deferred FileVault 2 enablement to be enforced at the login window, rather than waiting for a logout or restart of the Mac in question.
The -forceatlogin option must be set with an accompanying numerical value. This numerical value governs how many times the account being enabled can choose to defer having the FileVault 2 encryption process begin. For example, running the following command with root privileges will set a maximum number of ten deferral opportunities:
fdesetup enable -defer /path/to/filename.plist -forceatlogin 10

If the user chooses to defer, they will need to select the Don’t Enable button in the dialog window when it will appear. They will also be informed of how many more times they can log in before FileVault 2 encryption must be enabled.

If immediate enforcement is desired, setting a value of zero will enforce FileVault 2 encryption at the next login. To do this, run the following command with root privileges:
fdesetup enable -defer /path/to/filename.plist -forceatlogin 0

The fdesetup commands shown above will enforce FileVault 2 enablement at both login and logout. If only enforcement at login is desired, the -dontaskatlogout option can be used. This will prevent a deferred FileVault 2 enablement to be enforced at logout. For example, running the following command with root privileges will enforce FileVault 2 encryption at the next login but not prompt the user on logout:
fdesetup enable -defer /path/to/filename.plist -forceatlogin 0 –dontaskatlogout
An important thing to keep in mind about the –defer option is that it enables one single user account at the time of turning on FileVault 2 encryption. The –defer option does not enable multiple user accounts and cannot be used to enable accounts once FileVault 2 encryption has been turned on.
Enabling Filevault 2 Encryption Using One Or Multiple Recovery Keys
Another capability of FileVault 2 in El Capitan is the ability to use the alphanumeric personal recovery key, an institutional recovery key using /Library/Keychains/FileVaultMaster.keychain, or both kinds of recovery key at the same time.
As seen in the earlier examples, fdesetup will provide the alphanumeric personal recovery key by default. To use the institutional recovery key, the -keychain flag needs to be used when enabling encryption:
fdesetup enable –keychain
The alphanumeric personal recovery key is displayed, but the encryption will also use the /Library/Keychains/FileVaultMaster.keychain institutional recovery key. In case recovery is needed, either recovery key will work to unlock or decrypt the encrypted drive.

If you want to specify that only the FileVaultMaster.keychain institutional recovery key be used, both the -keychain and -norecoverykey flags need to be used when enabling encryption:
fdesetup enable -keychain –norecoverykey
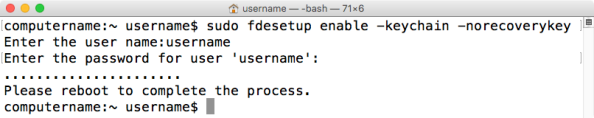
fdesetup is also capable of creating an institutional recovery key, using the -certificate flag to import an existing FileVault 2 public key. Once imported, fdesetup will automatically create a FileVaultMaster.keychain file to store the public key and save the keychain to /Library/Keychains.
The public key will need to be available as a DER encoded .cer certificate file. Once the certificate is available, the following command can be run with root privileges to enable FileVault 2, automatically create the institutional recovery key with the supplied public key and store it as /Library/Keychains/FileVaultMaster.keychain:
fdesetup enable -certificate /path/to/filename.cer
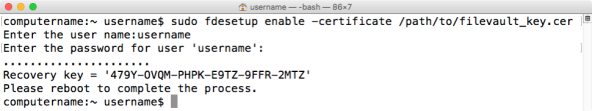
To specify that only the FileVaultMaster.keychain institutional recovery key be used, add the -norecoverykey flag to the command:
fdesetup enable -certificate /path/to/filename.cer -norecoverykey

It is also possible to include the public key data in a plist file, which allows the use of a plist to set up the institutional recovery key. The plist needs to follow the format below:
Using the public key’s DER encoded certificate file, the public key data for the plist can be obtained using the base64 tool by using the following command:
base64 /path/to/filename.cer > /path/to/filename.txt
At this point, you would copy the data string contained in the text file and place it into the Certificate value area of the plist file. You would store either the password of an existing FileVault 2-enabled user or (if available) an existing personal recovery key in the Password key in the plist.
Forcing A Restart When Enabling Filevault 2 Encryption
Along with the various options for enabling, it’s also possible to force a restart of the Mac once FileVault 2 has been successfully configured. This can help automate the process of enabling FileVault 2 on a Mac if no input from a logged-in user is needed.
For example, an institution may want to pre-configure its Macs to automatically encrypt with FileVault 2 at first boot with a local admin account enabled. It also wants to use only the institutional recovery key. If a plist with the desired account information and public key data to create the institutional recovery key is available, the following command could be run with root privileges to enable FileVault 2 and force a restart at the first boot:
fdesetup enable -inputplist < /path/to/filename.plist -norecoverykey -forcerestart
Once fdesetup had finished enabling the accounts in the plist file and creating /Library/Keychains/FileVaultMaster.keychain, the Mac would immediately restart and display the enabled accounts at the pre-boot login screen.
If you want to use the alphanumeric personal recovery key with -forcerestart, you will also need to output the personal recovery key and other information into a plist file. Taking the example above, the institution’s automated setup would run the following command with root privileges to automatically encrypt with FileVault 2 at first boot using both types of recovery key and a local admin account enabled:
fdesetup enable -inputplist < /path/to/filename.plist -outputplist > /path/to/recoverykeyinfo.plist –forcerestart
Disabling Filevault 2 Encryption
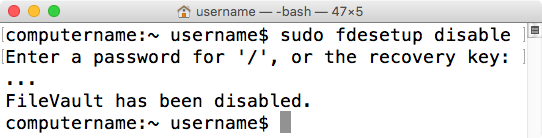
In contrast to all of the various options available for enabling FileVault 2 using fdesetup, the command to turn off FileVault 2 encryption is the following:
fdesetup disable
Adding Additional Users After Filevault 2 Has Been Enabled
Once FileVault 2 has been enabled, you can add additional users using fdesetup. To do so, you will need to a) wait until the FileVault 2 encryption has completed and b) provide both the username and password of a previously enabled account as well as the password of the account you want to add. The following command run with root privileges will enable a user account named otheruser:
fdesetup add -usertoadd otheruser

For those who want to automate the process, fdesetup also supports importing a properly formatted plist via a standard input stream (stdin). The plist needs to follow the format below:
When adding additional users using a plist file, the top level Username key is ignored, and the Password key value should either be an existing FileVault user’s password or the existing personal recovery key. Additional users can be added as needed by adding additional user information under the AdditionalUsers plist key.
Note: All account passwords need to be supplied in cleartext.
Once the plist has been set up and properly formatted, run the following command with root privileges to add additional users by referencing the account information in the plist file:
fdesetup add -inputplist < /path/to/filename.plist
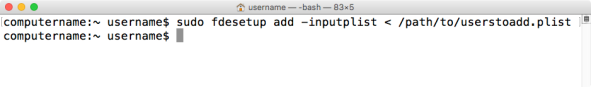
Listing Current Filevault 2 Users
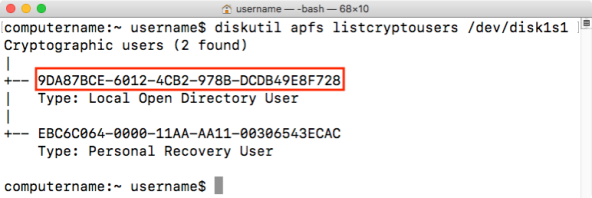
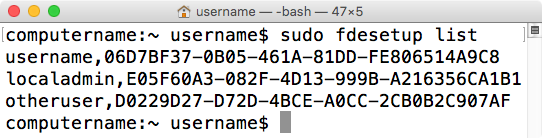
To list all accounts enabled for FileVault 2, run the following command with root privileges:
fdesetup list
All accounts will be listed with both the accounts’ username and UUID
Removing Users From The List Of Filevault 2 Enabled Accounts
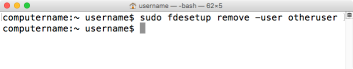
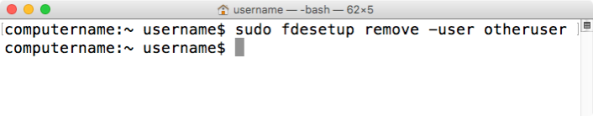
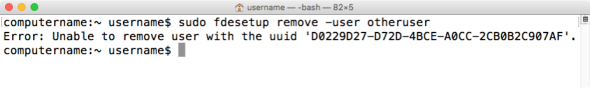
You can remove users from the list of FileVault enabled accounts by using either their username or the account’s UUID. To remove the account using the username, run the following command with root privileges:
fdesetup remove -user username_goes_here
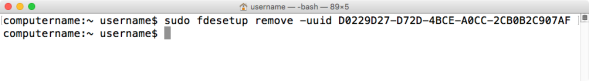
To remove the account using the account’s UUID, run the following command with root privileges:
fdesetup remove -uuid UUID_here
In both cases, successful removal of the account will not produce any additional output. If the account being removed is not currently enabled for use with FileVault 2, an error message will be displayed.
Managing Individual And Institutional Recovery Keys
fdesetup in El Capitan includes the ability to change, add and remove both personal and institutional recovery keys. This gives Mac admins much greater ability to manage recovery keys, including the capability to quickly update or remove compromised personal and/or institutional recovery keys in the event of a data breach or other problem.
You can add or change recovery keys using fdesetup changerecovery. To change to a new personal key, run the following command with root privileges:
fdesetup changerecovery -personal
You’ll be prompted for the password of an existing FileVault 2-enabled user or the existing personal recovery key. Once entered, a new personal recovery key will be generated and displayed. The former personal recovery key will no longer work.

For those who want to automate the process, fdesetup also supports importing a properly formatted plist via a standard input stream (stdin). The plist needs to follow the format below:
You would store either the password of an existing FileVault 2-enabled user or the existing personal recovery key in the Password key in the plist.
Once the plist has been set up and properly formatted, run the following command with root privileges to change to a new personal recovery key and reference the password or recovery key in the plist file:
fdesetup changerecovery -personal -inputplist < /path/to/filename.plist

In the event that the Mac in question does not have a personal recovery key, running the commands above will add a personal recovery key instead of changing an existing one.
To change to a new institutional recovery key, you will need to have the new public key available. If you have a new institutional public key available as a DER encoded certificate file, you can run the following command with root privileges to replace the current institutional key:
fdesetup changerecovery -institutional -keychain -certificate /path/to/filename.cer
If an institutional keychain is being used on this Mac, you will see a message that an existing FileVault Master keychain was found and moved. The reason for this is that, as part of this process, the current institutional key’s /Library/Keychains/FileVaultMaster.keychain file is replaced with a new /Library/Keychains/FileVaultMaster.keychain file that includes the new institutional recovery key’s public key.

While the former institutional key’s /Library/Keychains/FileVaultMaster.keychain was moved and not deleted, the former institutional recovery key will no longer work.
For those who want to automate the process, fdesetup also supports importing a properly formatted plist via a standard input stream (stdin). The plist needs to follow the format below:
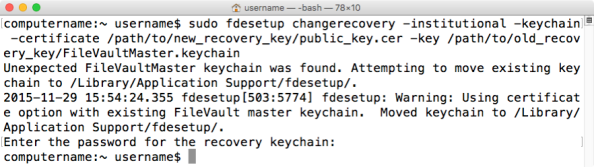
You can also use the current institutional recovery key to authenticate the change to the new institutional key. If you have a keychain file available containing the private key of the current institutional key, you can run the following command with root privileges to replace the current institutional key:
fdesetup changerecovery -institutional -keychain -certificate /path/to/filename.cer -key /path/to/filename.keychain
You’ll be prompted for the keychain’s password. Once entered, the current institutional key will be replaced with the new one.
In the event that the Mac in question does not have an institutional recovery key, running the commands above (with the exception of using the current institutional key for authentication) will add a institutional recovery key instead of changing an existing one.
Removing Individual And Institutional Recovery Keys
You can remove recovery keys using fdesetup removerecovery. To remove the current personal recovery key, run the following command with root privileges:
fdesetup removerecovery -personal
You’ll be prompted for the password of an existing FileVault 2-enabled user or the existing personal recovery key. Once entered, the personal recovery key will be removed from the system. The former personal recovery key will no longer work.

For those who want to automate the process, fdesetup also supports importing a properly formatted plist via a standard input stream (stdin). The plist needs to follow the format below:
You would store either the password of an existing FileVault 2-enabled user or the existing personal recovery key in the Password key in the plist.
Once the plist has been set up and properly formatted, run the following command with root privileges to remove the current personal recovery key and reference the password or recovery key in the plist file:
fdesetup removerecovery -personal -inputplist < /path/to/filename.plist

To remove institutional recovery keys, run the following command with root privileges:
fdesetup removerecovery -institutional
You’ll be prompted for the password of an existing FileVault 2-enabled user, or a personal recovery key if one is available. Once entered, the institutional recovery key will be removed from the system and will no longer work.

The removal of the institutional key can also be automated using a properly formatted plist via a standard input stream (stdin). The plist is the same as the one used for removing the personal key.
Once the plist has been set up and properly formatted, run the following command with root privileges to remove the institutional recovery key and reference the password or recovery key in the plist file:
fdesetup removerecovery -institutional -inputplist < /path/to/filename.plist
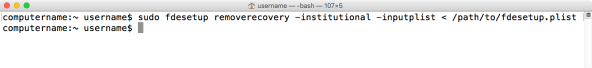
You can also use the recovery key associated with an institutional key to authenticate the removal of that institutional key. Once authenticated, the institutional key is removed from the system and will no longer work.
If you have a keychain file containing the private key for the current institutional key available, you can run the following command with root privileges to remove the current institutional key:
fdesetup removerecovery -institutional -key /path/to/filename.keychain

It is possible to use fdesetup removerecovery to remove one or both recovery keys on a particular Mac. Once the recovery keys are removed, the only way to unlock the FileVault 2 encryption is by using the password of an enabled account. That said, you could use fdesetup changerecovery to add one or both types of recovery keys back to the encrypted Mac.
Recovery Key Reporting
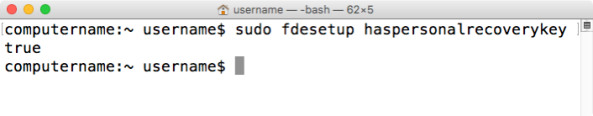
To go along with the ability to manage recovery keys, fdesetup in El Capitan enables Mac admins to detect which types of recovery keys are in use on a particular Mac. To check if a personal recovery key is in use, run the following command with root privileges:
fdesetup haspersonalrecoverykey
If FileVault 2 is using a personal recovery key, this command will return true. Otherwise it will return false.
To check if an institutional recovery key is in use, run the following command with root privileges:
fdesetup hasinstitutionalrecoverykey
If FileVault 2 is using an institutional recovery key, this command will return true. Otherwise it will return false.

One-Time Filevault 2 Encryption Bypass
fdesetup in El Capitan has the authrestart verb, which allows a FileVault 2-encrypted Mac to restart, bypass the FileVault 2 pre-boot login screen, and goes straight to the OS login window. To restart and bypass the FileVault 2 pre-boot login screen, run the following command with root privileges:
fdesetup authrestart
When the fdesetup authrestart command is run, it asks for the password of an existing FileVault 2-enabled user or a personal recovery key.
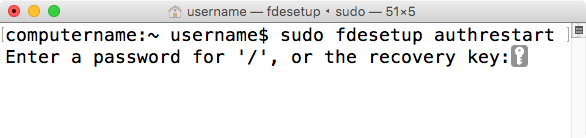
Once authenticated, the authrestart process puts an unlock key in system memory and reboots. On reboot, the reboot process automatically clears the unlock key from memory.
It’s also possible to automate this process by importing the authentication via a properly formatted plist. The plist needs to follow the format below:
Either the password of an existing FileVault 2-enabled user or a personal recovery key would be stored in the Password key in the plist.
Once the plist has been set up and properly formatted, use the following command with root privileges to run the authrestart process and reference the password or recovery key in the plist file for authentication:
fdesetup authrestart -inputplist < /path/to/filename.plist

fdesetup authrestart may not be supported by all El Capitan-compatible Macs. To verify if a specific Mac supports authrestart, run the following command with root privileges:
fdesetup supportsauthrestart
If the Mac supports fdesetup authrestart, this command will return true. Otherwise it will return false.

The authrestart function can also be leveraged part of enabling FileVault 2 encryption. To re-use a previous example, an institution may want to pre-configure its Macs to automatically encrypt with FileVault 2 at first boot with a local admin account enabled and using only an institutional recovery key. It also wants the Macs to bypass the login screen and boot normally, so that the encryption process can continue unattended.
If a plist with the desired account information and public key data to create the institutional recovery key is available, the following command could be run with root privileges to enable FileVault 2, automatically reboot the Mac, bypass the FileVault 2 pre-boot login screen and boot normally to the OS login window.
fdesetup enable -authrestart -inputplist < /path/to/filename.plist -norecoverykey
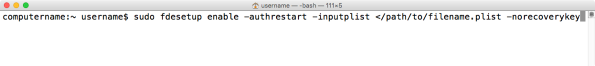
Once fdesetup had finished enabling the accounts in the plist file and creating /Library/Keychains/FileVaultMaster.keychain, the Mac would immediately restart, bypass the pre-boot login screen and boot the OS. The encryption of the boot volume would proceed normally after the reboot.
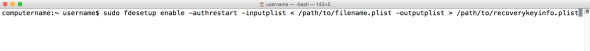
If using the alphanumeric personal recovery key with -authrestart, the personal recovery key and other information will need to be exported to a plist file. Taking the example above, the institution’s automated setup would run the following command with root privileges to automatically encrypt with FileVault 2 at first boot using both types of recovery key and a local admin account enabled:
fdesetup enable -authrestart -inputplist < /path/to/recoverykeyinfo.plist -outputplist > /path/to/recoverykeyinfo.plist
Reporting On Filevault 2 Encryption Or Decryption Status
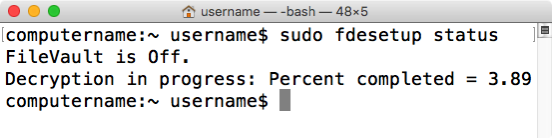
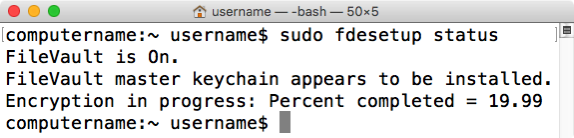
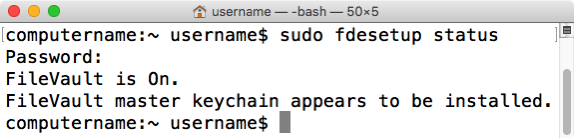
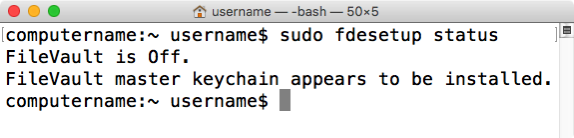
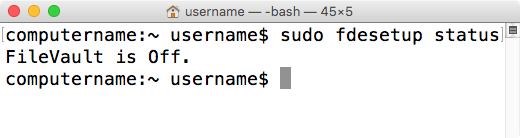
fdesetup can report on FileVault 2 encryption or decryption status. Running the following command with root privileges will display the current state:
fdesetup status
Conclusion
fdesetup in El Capitan is a solid tool for FileVault 2 management, with the abilities to enable FileVault 2, add and remove users from the list of FileVault 2 authorized accounts, manage recovery keys, report on FileVault 2’s status and more. Among its greatest strengths are:
- It allows options for automating FileVault 2 setups via scripting.
- fdesetup’s deferred enablement option can be used to set up a self-service procedure for enabling encryption either at login or logout.
- It supports multiple recovery keys for FileVault 2, giving Mac admins more options for handling recovery situations.
- It allows you to rotate or remove recovery keys on an as-needed basis.
- It provides a one-time method for bypassing encryption on restart, to accommodate situations where an encrypted Mac needs to be restarted from a remote location.
Managing FileVault 2 encryption using this tool will save you time and give encryption options available with no other software.